Differenze tra le versioni di "AdminGuide:BasicConcepts:Users and roles/en"
| (18 versioni intermedie di 4 utenti non mostrate) | |||
| Riga 5: | Riga 5: | ||
= Users = | = Users = | ||
Access to KalliopePBX GUI (as well as CTI services, LDAP phonebook, etc.) is granted to '''users'''. There are two kinds of users: '''built-in''' and '''custom''' users. '''Built-in users''' include administrative and service users, whose roles are usually predefined and not modifiable, whereas '''custom users''' are additional users that can be created and assigned to custom roles. | Access to the KalliopePBX GUI (as well as CTI services, LDAP phonebook, etc.) is granted to '''users'''. There are two kinds of users: '''built-in''' and '''custom''' users. '''Built-in users''' include administrative and service users, whose roles are usually predefined and not modifiable, whereas '''custom users''' are additional users that can be created and assigned to custom roles. | ||
Each user has one or more associated access permissions among GUI, CTI, and API. | Each user has one or more associated access permissions among GUI, CTI, and API. | ||
| Riga 13: | Riga 13: | ||
== Built-in users == | == Built-in users == | ||
The first example of built-in user is '''admin''' (whose default password is "admin"), used to access the GUI after the first firmware installation. This is the primary technical figure | The first example of the built-in user is '''admin''' (whose default password is "admin"), used to access the GUI after the first firmware installation. This is the primary technical figure and is commonly used to perform the system configuration. Additional users may have the rights to perform configuration tasks, but they can be limited to specific GUI panels only, according to their granted '''Role'''. | ||
The following table lists the built-in users along with their access permissions. (Note: (+) means that this access permission is assigned and cannot be revoked; (-) | The following table lists the built-in users along with their access permissions. (Note: (+) means that this access permission is assigned and cannot be revoked; (-) indicates that the consent can be granted or not.) | ||
{| class="wikitable" | {| class="wikitable" | ||
| Riga 33: | Riga 33: | ||
! phonebook | ! phonebook | ||
| style="text-align:center;" | GUI (-)<br />API (-) | | style="text-align:center;" | GUI (-)<br />API (-) | ||
| This user has read access to the KalliopePBX phonebook. It has to be explicitly enabled from the "System Settings" -> [[AdminGuide: | | This user has read access to the KalliopePBX phonebook. It has to be explicitly enabled from the "System Settings" -> [[AdminGuide:BasicConcepts:Users_and_roles/en#Users|"Users Management"]] panel, assigning it a password and the required access permissions. N.B.: GUI permission also grants the right to access the integrated LDAP server, where the KalliopePBX phonebook is published (according to the settings in "Phonebook"->"LDAP Settings" panel). The "phonebook" user is mainly useful to have a single identity (configurable through provisioning) used by telephones to access the KalliopePBX phonebook using LDAP. | ||
|- | |- | ||
! click2call | ! click2call | ||
| Riga 42: | Riga 42: | ||
=== Multi-tenant === | === Multi-tenant === | ||
During Multitenant license activation, the PBX and the tenant entities, | During Multitenant license activation, the PBX and the tenant entities, bundled under a single administrative entity, are separated and a new built-in user '''pbxadmin''' is created (with default password "admin"). | ||
Management of the PBX as a system is granted to the new "pbxadmin" user, who has both GUI and CTI permissions, whereas the "admin" user retains control of the telephone service configuration for the tenant. Since multiple tenants can be created, each with its own "admin", it is necessary to extend the username to specify the relevant tenant domain. The predefined existing tenant domain is "default", so the predefined | Management of the PBX as a system is granted to the new "pbxadmin" user, who has both GUI and CTI permissions, whereas the "admin" user retains control of the telephone service configuration for the tenant. Since multiple tenants can be created, each with its own "admin", it is necessary to extend the username to specify the relevant tenant domain. The predefined existing tenant domain is "default", so the predefined built-in users become admin@default, privacyadmin@default, etc. | ||
For each new tenant created (e.g. with domain "sampledomain"), | For each new tenant created (e.g. with domain "sampledomain"), several new users are generated, namely admin@sampledomain, privacyadmin@sampledomain, phonebook@sampledomain, and so on. | ||
The admin@default and admin@sampledomain users are completely independent and each one can only manage their own tenant. | The admin@default and admin@sampledomain users are completely independent and each one can only manage their own tenant. | ||
'''N.B.''': if a user does not specify the domain when logging in (e.g. uses "admin" instead of "admin@somedomain"), then it is assumed to belong to the default domain and authentication is performed accordingly. | '''N.B.''': if a user does not specify the domain when logging in (e.g. uses "admin" instead of "admin@somedomain"), then it is assumed to belong to the default domain and authentication is performed accordingly. | ||
| Riga 54: | Riga 54: | ||
== Custom users == | == Custom users == | ||
Additional users can be created. Currently, custom users | Additional users can be created. Currently, custom users must be associated with an '''Extension'''. Custom users can be created in the "Edit Extension" panel, defining a unique username (within the tenant) and assigning GUI, CTI and/or API access permissions. By default, all custom users are created with the standard "Tenant User" role, but a different one can be selected among those available. As detailed below, roles are managed in the "System Settings" -> "[[AdminGuide:GUI:OperatingMenu:RolesManagement/en|Roles Management]]" panel, where different access permissions (none/list/read/write) can be assigned for each panel of the GUI, allowing the admin to delegate some configuration tasks to selected users. | ||
Once created, custom users cannot be edited from the "Edit extension" panel, but they appear in the "System Settings" -> [[AdminGuide: | == Users configuration == | ||
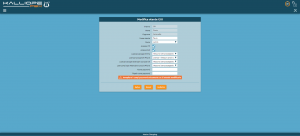
[[File:Utenti GUI.png|miniatura]] | |||
During the creation of an [[AdminGuide:BasicConcepts:Extensions and SIP accounts/en|extension]], the ''create local user'' box is selected and a new GUI [[AdminGuide:BasicConcepts:Users and roles/en|user]] is automatically created with the credentials set during creation. | |||
To edit and manage these [[AdminGuide:BasicConcepts:Users and roles/en|users]], you need to access the ''GUI users management'' in the ''System settings'' menu. | |||
Through the [[AdminGuide:BasicConcepts:Users and roles/en|users]] configuration page, you can: | |||
* edit the credentials (username and password) necessary to access the GUI and the clients; | |||
* assign a [[AdminGuide:GUI:OperatingMenu:RolesManagement/en|role]] and the relative read/write permissions; | |||
* enable/disable access to the GUI and the clients; | |||
* assign the following licenses: KalliopeCTI Pro, KalliopeCTI Phone, Kalliope Attendant Console CTI, Kalliope Attendant Console Phone. | |||
Once created, custom users cannot be edited from the "Edit extension" panel, but they appear in the "System Settings" -> [[AdminGuide:BasicConcepts:Users_and_roles/en|"Users Management"]] panel, along with the built-in ones. | |||
== User authentication == | == User authentication == | ||
| Riga 68: | Riga 81: | ||
= Roles = | = Roles = | ||
Each user is assigned a role, which determines their permissions in terms of access to the various panels. | Each user is assigned a role, which determines their permissions in terms of access to the various panels. Since their permissions are fixed, built-in users have built-in roles (currently not assignable to custom users). | ||
Custom users by default have the "Tenant User" (or simply "User") role, which is | Custom users by default have the "Tenant User" (or simply "User") role, which is built-in and not modifiable. This role grants the user the right to access their own CDR and the local, shared, and personal phonebooks. | ||
Additional roles ("Power User" roles) can be created and assigned to the custom users. Each role has a priority attribute (an integer value between 1 and 99; standard users have priority 0, whereas tenant admin has 100) which is used to resolve contention of the Configuration Lock when multiple users need to perform configuration operations on the PBX. Users can acquire the Configuration Lock even if it is currently held by another user, provided that their role priority is higher than the one of the user currently holding the lock. Note that the action of acquiring the lock currently held by another user drops all the pending changes made by the first user. | Additional roles ("Power User" roles) can be created and assigned to the custom users. Each role has a priority attribute (an integer value between 1 and 99; standard users have priority 0, whereas tenant admin has 100) which is used to resolve contention of the Configuration Lock when multiple users need to perform configuration operations on the PBX. Users can acquire the Configuration Lock even if it is currently held by another user, provided that their role priority is higher than the one of the user currently holding the lock. Note that the action of acquiring the lock currently held by another user drops all the pending changes made by the first user. | ||
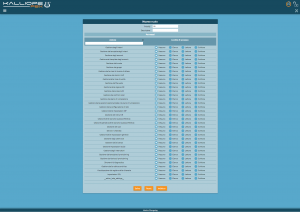
Custom roles | == Roles configuration == | ||
* "none": the user cannot access | |||
* "list": the user has read | [[File:Pagina Ruoli.png|miniatura]] | ||
* "read": the user can access the list panel | |||
* "write": user has full read | To configure a role, you must first set a priority from 0 to 99. Users with higher priority can acquire the lock from power priority users, and unsaved changes will be lost. | ||
Custom roles can be configured by selecting the level of access to each panel from those available: | |||
Custom roles can be configured by selecting the level of access to each panel from those available: | |||
* "none": the user cannot access the panel and the link to the panel will not be displayed in the navigation menu (direct access to the panel URL is also blocked) | |||
* "list": the user has read access to the panel with the list of related entities (for example, the extension list) but cannot access the details of each item or perform actions on them | |||
* "read": the user can access both the list panel and those of the individual entries, but only in read mode | |||
* "write": the user has full read/write access to the related entities | |||
The following table lists the configurable parameters for each role. | |||
{| class="wikitable" | |||
|- | |||
! <div style = 'text-align: left> '''Parameter''' !! <div style = 'text-align: left> '''Description''' !! <div style = 'text-align: left> '''Value''' | |||
|- | |||
|colspan="3"| <div style = 'text-align: center; color: transparent> - | |||
|- | |||
| Priority || Priority assigned to the role. || Numeric (from 0 to 99) | |||
|- | |||
| Description || Role identifier. || Alphanumeric | |||
|- | |||
!colspan="3"| <div style = 'text-align: left> '''''Permissions''''' | |||
|- | |||
| [[AdminGuide:BasicConcepts:Extensions_and_SIP_accounts/en#Extensions_configuration|Extension management]] || Enable users to manage extensions with the selected permissions. || rowspan="34"| None / List / Read / Write | |||
|- | |||
| Extension template management || Enable users to manage extension templates with the selected permissions. | |||
|- | |||
| [[AdminGuide:BasicConcepts:Extensions_and_SIP_accounts/en#Account_configuration|Account management]] || Enable users to manage accounts with the selected permissions. | |||
|- | |||
| Account template management || Enable users to manage account templates with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:ACD/en|Queue management]]|| Enable users to manage queues with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:RingGroups/en|Ring group management]] || Enable users to manage ring groups with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:AudioFile/en#Music_On_Hold_Classes_Configuration|Music on hold class management]] || Enable users to manage music on hold classes with the selected permissions. | |||
|- | |||
| [[AdminGuide:BasicConcepts:Outbound_lines:Dominio_VoIP/en|VoIP domain management]] || Enable users to manage VoIP domains with the selected permissions. | |||
|- | |||
| [[AdminGuide:BasicConcepts:Outbound_lines/en#Configuration|Outbound line management]] || Enable users to manage outbound lines with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:AudioFile/en|Audio file management]] || Enable users to manage audio files with the selected permissions. | |||
|- | |||
| LCR rule management || Enable users to manage LCR rules with the selected permissions. | |||
|- | |||
| LCR class || Enable users to manage LCR classes with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:ChecktimeAndSwitches/en#Configuration_of_Checktime| Checktime management]] || Enable users to manage time checks with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:NumberingPlan/en|Numbering plan management]] || Enable users to manage the numbering plan with the selected permissions. | |||
|- | |||
| Management of the custom selections in the numbering plan || Enable users to manage custom selections with the selected permissions. | |||
|- | |||
| Network configuration management || Enable users to manage network configuration with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:SIPSettings/en|SIP setting management]] || Enable users to manage SIP settings with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:IVR/en|IVR menu management]] || Enable users to manage IVR menus with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:MeetMe/en|Audio conference room management]] || Enable users to manage audio conference rooms with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:MeetMe/en|Audio conference room operation management]]|| Enable users to manage audio conference room operation with the selected permissions. | |||
|- | |||
| Role management || Enable users to manage roles with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:OnCallServices/en|On-call service management]] || Enable users to manage on-call services with the selected permissions. | |||
|- | |||
| [[AdminGuide:GUI:OperatingMenu:GeneralSettings/en|General setting management]] || Enable users to manage general settings with the selected permissions. | |||
|- | |||
| [[AdminGuide:BasicConcepts:Users_and_roles/en#Users_configuration|GUI user management]] || Enable users to manage GUI users with the selected permissions. | |||
|- | |||
| [[AdminGuide:BasicConcepts:Licenses/en|License management]] || Enable users to manage licenses with the selected permissions. | |||
|- | |||
| Audio setting management || Enable users to manage audio settings with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:ChecktimeAndSwitches/en|Switch management]] || Enable users to manage switches with the selected permissions. | |||
|- | |||
| Provisioning template management || Enable users to manage provisioning templates with the selected permissions. | |||
|- | |||
| Provisioning device management || Enable users to manage provisioning devices with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:PacketCapture/en|Diagnostic tool management]] || Enable users to manage diagnostic tools with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:Phonebook/en#Shared_phonebook|Shared phonebook management]] || Enable users to manage shared phonebook with the selected permissions. | |||
|- | |||
| Call detail record viewing || Enable users to view the call detail record. | |||
|- | |||
| [[AdminGuide:Service:SSLSettings/en|SSL setting management]] || Enable users to manage SSL settings with the selected permissions. | |||
|- | |||
| [[AdminGuide:Service:Phonebook/en#LDAP_settings|LDAP setting management]] || Enable users to manage LDAP settings with the selected permissions. | |||
|} | |||
Versione attuale delle 16:01, 19 set 2022
Return to AdminGuide:BasicConcepts
Users
Access to the KalliopePBX GUI (as well as CTI services, LDAP phonebook, etc.) is granted to users. There are two kinds of users: built-in and custom users. Built-in users include administrative and service users, whose roles are usually predefined and not modifiable, whereas custom users are additional users that can be created and assigned to custom roles.
Each user has one or more associated access permissions among GUI, CTI, and API.
- GUI: GUI access means that the user can log into the KalliopePBX web interface; GUI access also grants the user permission to access the integrated LDAP server.
- CTI: CTI access allows the users to use Kalliope applications (CTI, Logger, Supervisor Panel) which connect to the PBX using the CTI socket and protocol.
- API: API access allows the users to invoke the KalliopePBX REST APIs available at http[s]://<PBX IP>/rest/ (see REST API).
Built-in users
The first example of the built-in user is admin (whose default password is "admin"), used to access the GUI after the first firmware installation. This is the primary technical figure and is commonly used to perform the system configuration. Additional users may have the rights to perform configuration tasks, but they can be limited to specific GUI panels only, according to their granted Role.
The following table lists the built-in users along with their access permissions. (Note: (+) means that this access permission is assigned and cannot be revoked; (-) indicates that the consent can be granted or not.)
| Username | Access permissions | Notes |
|---|---|---|
| admin | GUI (+) CTI (+) API (+) |
This is the main technical user. They have full privileges on PBX configuration both for system (network, network services) and telephony (entities, services, etc.). They have full access to logs and records, but they have some limitations regarding aspects related to the privacy of the users. Firstly, they cannot see the external telephone numbers in the CDR in full, but are only able to view them with last three digits replaced by "xxx"; secondly, the "admin" user does not have access to Call Recording configuration and files, which is limited to "privacyadmin" user (and delegated users). |
| privacyadmin | GUI (-) API (-) |
This user has full access to the external telephone numbers of the CDR, and is the only one who can configure call recording authorization. They can also access call recording records, download and listen to the recorded calls, as well as grant other users "privacy" permissions, which gives them access to full numbers in CDR and to the list of recorded calls and the corresponding files. |
| phonebook | GUI (-) API (-) |
This user has read access to the KalliopePBX phonebook. It has to be explicitly enabled from the "System Settings" -> "Users Management" panel, assigning it a password and the required access permissions. N.B.: GUI permission also grants the right to access the integrated LDAP server, where the KalliopePBX phonebook is published (according to the settings in "Phonebook"->"LDAP Settings" panel). The "phonebook" user is mainly useful to have a single identity (configurable through provisioning) used by telephones to access the KalliopePBX phonebook using LDAP. |
| click2call | GUI (-) API (-) |
This user is useful when using third party applications to send click-to-call commands (using the REST API /rest/phoneServices/c2c/{dest_exten}/{source_exten}) to KalliopePBX using a single user with limited privileges |
Multi-tenant
During Multitenant license activation, the PBX and the tenant entities, bundled under a single administrative entity, are separated and a new built-in user pbxadmin is created (with default password "admin").
Management of the PBX as a system is granted to the new "pbxadmin" user, who has both GUI and CTI permissions, whereas the "admin" user retains control of the telephone service configuration for the tenant. Since multiple tenants can be created, each with its own "admin", it is necessary to extend the username to specify the relevant tenant domain. The predefined existing tenant domain is "default", so the predefined built-in users become admin@default, privacyadmin@default, etc.
For each new tenant created (e.g. with domain "sampledomain"), several new users are generated, namely admin@sampledomain, privacyadmin@sampledomain, phonebook@sampledomain, and so on.
The admin@default and admin@sampledomain users are completely independent and each one can only manage their own tenant.
N.B.: if a user does not specify the domain when logging in (e.g. uses "admin" instead of "admin@somedomain"), then it is assumed to belong to the default domain and authentication is performed accordingly.
Custom users
Additional users can be created. Currently, custom users must be associated with an Extension. Custom users can be created in the "Edit Extension" panel, defining a unique username (within the tenant) and assigning GUI, CTI and/or API access permissions. By default, all custom users are created with the standard "Tenant User" role, but a different one can be selected among those available. As detailed below, roles are managed in the "System Settings" -> "Roles Management" panel, where different access permissions (none/list/read/write) can be assigned for each panel of the GUI, allowing the admin to delegate some configuration tasks to selected users.
Users configuration
During the creation of an extension, the create local user box is selected and a new GUI user is automatically created with the credentials set during creation.
To edit and manage these users, you need to access the GUI users management in the System settings menu.
Through the users configuration page, you can:
- edit the credentials (username and password) necessary to access the GUI and the clients;
- assign a role and the relative read/write permissions;
- enable/disable access to the GUI and the clients;
- assign the following licenses: KalliopeCTI Pro, KalliopeCTI Phone, Kalliope Attendant Console CTI, Kalliope Attendant Console Phone.
Once created, custom users cannot be edited from the "Edit extension" panel, but they appear in the "System Settings" -> "Users Management" panel, along with the built-in ones.
User authentication
User authentication is performed with a password check, using one of the two available authentication methods.
The first method is "Local Authentication": the user password is handled by the PBX, and its hash is stored in the internal database for authentication. This is the only available authentication method for the "admin" user.
KalliopePBX can also authenticate users with external services; the supported external authentication services are Microsoft Active Directory and LDAP servers. External authentication services are defined on a per-tenant basis, so they need to handle usernames of the form "user@tenant_domain".
Roles
Each user is assigned a role, which determines their permissions in terms of access to the various panels. Since their permissions are fixed, built-in users have built-in roles (currently not assignable to custom users).
Custom users by default have the "Tenant User" (or simply "User") role, which is built-in and not modifiable. This role grants the user the right to access their own CDR and the local, shared, and personal phonebooks.
Additional roles ("Power User" roles) can be created and assigned to the custom users. Each role has a priority attribute (an integer value between 1 and 99; standard users have priority 0, whereas tenant admin has 100) which is used to resolve contention of the Configuration Lock when multiple users need to perform configuration operations on the PBX. Users can acquire the Configuration Lock even if it is currently held by another user, provided that their role priority is higher than the one of the user currently holding the lock. Note that the action of acquiring the lock currently held by another user drops all the pending changes made by the first user.
Roles configuration
To configure a role, you must first set a priority from 0 to 99. Users with higher priority can acquire the lock from power priority users, and unsaved changes will be lost.
Custom roles can be configured by selecting the level of access to each panel from those available:
Custom roles can be configured by selecting the level of access to each panel from those available:
- "none": the user cannot access the panel and the link to the panel will not be displayed in the navigation menu (direct access to the panel URL is also blocked)
- "list": the user has read access to the panel with the list of related entities (for example, the extension list) but cannot access the details of each item or perform actions on them
- "read": the user can access both the list panel and those of the individual entries, but only in read mode
- "write": the user has full read/write access to the related entities
The following table lists the configurable parameters for each role.
Parameter |
Description |
Value
|
|---|---|---|
-
| ||
| Priority | Priority assigned to the role. | Numeric (from 0 to 99) |
| Description | Role identifier. | Alphanumeric |
Permissions
| ||
| Extension management | Enable users to manage extensions with the selected permissions. | None / List / Read / Write |
| Extension template management | Enable users to manage extension templates with the selected permissions. | |
| Account management | Enable users to manage accounts with the selected permissions. | |
| Account template management | Enable users to manage account templates with the selected permissions. | |
| Queue management | Enable users to manage queues with the selected permissions. | |
| Ring group management | Enable users to manage ring groups with the selected permissions. | |
| Music on hold class management | Enable users to manage music on hold classes with the selected permissions. | |
| VoIP domain management | Enable users to manage VoIP domains with the selected permissions. | |
| Outbound line management | Enable users to manage outbound lines with the selected permissions. | |
| Audio file management | Enable users to manage audio files with the selected permissions. | |
| LCR rule management | Enable users to manage LCR rules with the selected permissions. | |
| LCR class | Enable users to manage LCR classes with the selected permissions. | |
| Checktime management | Enable users to manage time checks with the selected permissions. | |
| Numbering plan management | Enable users to manage the numbering plan with the selected permissions. | |
| Management of the custom selections in the numbering plan | Enable users to manage custom selections with the selected permissions. | |
| Network configuration management | Enable users to manage network configuration with the selected permissions. | |
| SIP setting management | Enable users to manage SIP settings with the selected permissions. | |
| IVR menu management | Enable users to manage IVR menus with the selected permissions. | |
| Audio conference room management | Enable users to manage audio conference rooms with the selected permissions. | |
| Audio conference room operation management | Enable users to manage audio conference room operation with the selected permissions. | |
| Role management | Enable users to manage roles with the selected permissions. | |
| On-call service management | Enable users to manage on-call services with the selected permissions. | |
| General setting management | Enable users to manage general settings with the selected permissions. | |
| GUI user management | Enable users to manage GUI users with the selected permissions. | |
| License management | Enable users to manage licenses with the selected permissions. | |
| Audio setting management | Enable users to manage audio settings with the selected permissions. | |
| Switch management | Enable users to manage switches with the selected permissions. | |
| Provisioning template management | Enable users to manage provisioning templates with the selected permissions. | |
| Provisioning device management | Enable users to manage provisioning devices with the selected permissions. | |
| Diagnostic tool management | Enable users to manage diagnostic tools with the selected permissions. | |
| Shared phonebook management | Enable users to manage shared phonebook with the selected permissions. | |
| Call detail record viewing | Enable users to view the call detail record. | |
| SSL setting management | Enable users to manage SSL settings with the selected permissions. | |
| LDAP setting management | Enable users to manage LDAP settings with the selected permissions. | |