Differenze tra le versioni di "AdminGuide:Service:SSLSettings/en"
(Creata pagina con "By default, on all Kalliope, there is a self-assigned certificate that is issued by a self-generated, in-house CA.") |
|||
| (7 versioni intermedie di 2 utenti non mostrate) | |||
| Riga 1: | Riga 1: | ||
<languages /> | <languages /> | ||
Return to [[AdminGuide:Service/en|AdminGuide:Service]] | Return to [[AdminGuide:Service/en|AdminGuide:Service]] | ||
| Riga 6: | Riga 7: | ||
== Configuration == | == Configuration == | ||
=== | [[File:System settings, ssl.png|400px|destra]] | ||
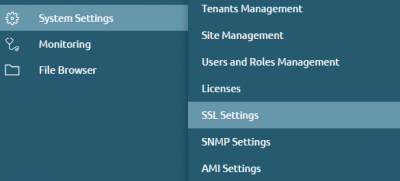
To reach the SSL settings section you can follow the path '''"System settings > SSL Settings"''' as shown in the right figure. | |||
=== Trusted CA Management === | |||
This section contains the list of Certification Authorities of phone vendors that the pbx considers valid to authenticate a client certificate. | This section contains the list of Certification Authorities of phone vendors that the pbx considers valid to authenticate a client certificate. | ||
The server certificate is rarely issued directly from one of the CAs on the phone, since they are no-root CAs. Often certificates are issued by intermediate CAs. | The server certificate is rarely issued directly from one of the CAs on the phone, since they are no-root CAs. Often certificates are issued by intermediate CAs. | ||
'''N.B. | '''N.B.''' It is important to remember the correct sequence of the chain: root CA > intermediate CA > server certificates | ||
| Riga 17: | Riga 21: | ||
You have to upload the server certificate consisting of the actual certificate and private key and the intermediate CAs that are used to build the chain of trust up to the root CA. | You have to upload the server certificate consisting of the actual certificate and private key and the intermediate CAs that are used to build the chain of trust up to the root CA. | ||
The certificates must be put together inside a single ''.pem | The certificates must be put together inside a single ''.pem'' file. | ||
The phone then provides the client certificate, the certificate is validated by the pbx using the trusted CAs in the panel. | The phone then provides the client certificate, the certificate is validated by the pbx using the trusted CAs in the panel. | ||
| Riga 31: | Riga 35: | ||
By default, on all Kalliope, there is a self-assigned certificate that is issued by a self-generated, in-house CA. | By default, on all Kalliope, there is a self-assigned certificate that is issued by a self-generated, in-house CA. | ||
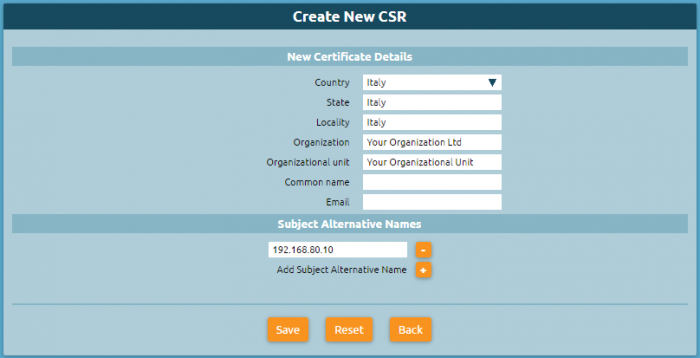
You can create a new CSR certificate (Certificate Signing Request) by clicking on "Create new CSR" and entering: | |||
the details of the new certificate: | the details of the new certificate: | ||
* | * Country | ||
* State | * State | ||
* | * Locality | ||
* | * Organization | ||
* | * Organizational unit | ||
* Common name | * Common name | ||
* E-mail | * E-mail | ||
[[File:Create new csr.PNG|700px]] | |||
=== Local CA Management === | |||
In this section you can observe the '''Root Certificate Details''' and the '''Certificates List'''. | |||
It is also possible to: | |||
* Emit new certificate and to insert: | |||
new certificate details and Subject Alternative Names: | |||
** Install as server certificate | |||
** Country | |||
** State | |||
** Locality | |||
** Organization | |||
** Organizational unit | |||
** Common name | |||
** E-mail | |||
* Download root certificate (.pem) | |||
* Download root certificate (.der) | |||
* Delete local CA | |||
Versione attuale delle 08:40, 21 set 2022
Return to AdminGuide:Service
Description
The SSL (Secure Sockets Layer) settings section contains the management of trusted CAs (Certification Authorities).
Configuration
To reach the SSL settings section you can follow the path "System settings > SSL Settings" as shown in the right figure.
Trusted CA Management
This section contains the list of Certification Authorities of phone vendors that the pbx considers valid to authenticate a client certificate.
The server certificate is rarely issued directly from one of the CAs on the phone, since they are no-root CAs. Often certificates are issued by intermediate CAs.
N.B. It is important to remember the correct sequence of the chain: root CA > intermediate CA > server certificates
The root CA issues a certificate to an intermediate CA and the intermediate CA issues the server certificates.
You have to upload the server certificate consisting of the actual certificate and private key and the intermediate CAs that are used to build the chain of trust up to the root CA.
The certificates must be put together inside a single .pem file. The phone then provides the client certificate, the certificate is validated by the pbx using the trusted CAs in the panel.
If the certificate is deemed valid and both the CN (common name) and MAC address match the file it is requesting, then everything matches, the session closes, and the download of the provisioning file can start.
While on browsers intermediate CAs are often preloaded, on phones, for reasons of memory occupancy there are only root CAs. If we load the server certificate signed by an intermediate (signed by a root CA) on the machine, but the server passes only its own certificate and not the intermediate one to the phone, it is not considered valid by the phone.
It is then necessary to upload both the intermediate CA and the server certificate.
Server certificate management
In this section you can upload the server certificate in a single .pem file.
By default, on all Kalliope, there is a self-assigned certificate that is issued by a self-generated, in-house CA.
You can create a new CSR certificate (Certificate Signing Request) by clicking on "Create new CSR" and entering:
the details of the new certificate:
- Country
- State
- Locality
- Organization
- Organizational unit
- Common name
Local CA Management
In this section you can observe the Root Certificate Details and the Certificates List.
It is also possible to:
- Emit new certificate and to insert:
new certificate details and Subject Alternative Names:
- Install as server certificate
- Country
- State
- Locality
- Organization
- Organizational unit
- Common name
- Download root certificate (.pem)
- Download root certificate (.der)
- Delete local CA